Stay One Step Ahead of Hackers
At Laraware, we offer web application penetration testing (WAPT) to help businesses proactively discover vulnerabilities in their web platforms before cybercriminals can exploit them. Our ethical hacking experts simulate real-world attack scenarios to assess your application’s defense against SQL injection, XSS, authentication flaws, insecure APIs, and other critical threats.
If you’re launching, scaling, or maintaining a web app—pen testing isn’t optional. It’s essential.
Deliverables You Can Act On
After the test, we provide a detailed report that includes:
Executive summary
List of vulnerabilities by risk level
Step-by-step reproduction methods
Recommended remediation for each issue
Compliance mapping (OWASP Top 10, ISO 27001, etc.)
Our Penetration Testing Process
At Laraware, we follow a systematic and ethical penetration testing methodology to simulate real-world cyberattacks and uncover vulnerabilities in your web applications. Our process helps your organization strengthen defenses before attackers find the weaknesses.
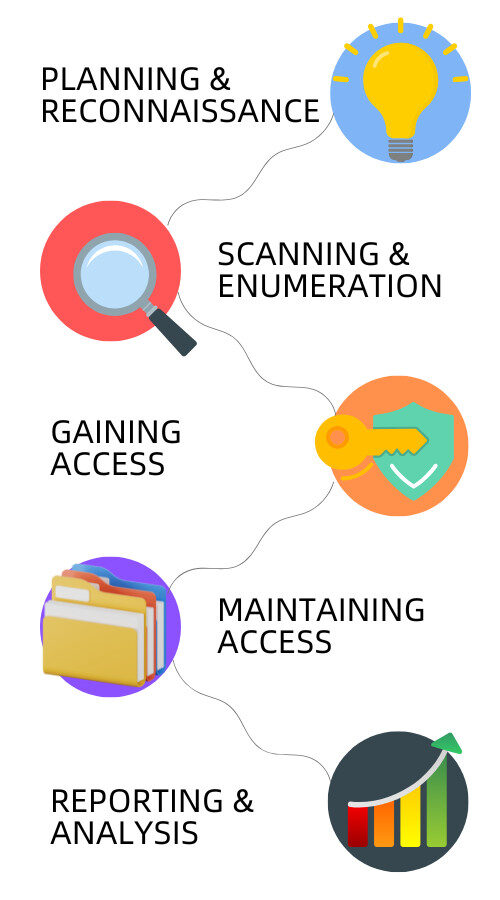
🔍 1. Planning & Reconnaissance
We begin by defining the scope, goals, and testing parameters. During this phase, our team gathers intelligence—such as domain names, IP addresses, and mail servers—to understand the target environment and identify potential entry points.
🧭 2. Scanning & Enumeration
We analyze how your application responds to intrusion attempts using:
Static Analysis: Reviewing source code to understand vulnerabilities in logic or structure.
Dynamic Analysis: Observing the app in runtime to identify flaws under real-world usage conditions.
🔓 3. Gaining Access
This is where our certified ethical hackers launch simulated attacks, such as:
SQL Injection
Cross-Site Scripting (XSS)
Insecure Authentication
Logic Bypass or Session Hijacking
We evaluate how these vulnerabilities can be exploited to access data, escalate privileges, or intercept sessions.
⏳ 4. Maintaining Access
We simulate Advanced Persistent Threats (APTs) to test how long an attacker could remain undetected in your system. This stage helps uncover weaknesses in monitoring, logging, and intrusion detection mechanisms.
📊 5. Reporting & Analysis
Our final step is a detailed, actionable report that includes:
Vulnerabilities exploited
Data accessed
Time spent inside the system undetected
Recommended remediation strategies
We help your teams prioritize and fix issues based on real business risk, not just technical severity.
What We Test
If your technology is draining resources rather than optimizing them, we can get you back on track. A professionally managed services provider can give you the decisive edge to:
Authentication & Access Control
Ensure user roles, sessions, and password systems are secure and protected from brute-force or privilege escalation.
Injection Vulnerabilities
Test for SQL injection, command injection, and LDAP injection threats across all input points.
Cross-Site Scripting (XSS)
Check for reflected, stored, and DOM-based XSS issues that could compromise user data and session hijacking.
Business Logic Errors
Identify loopholes in workflows and user interactions that could be abused to bypass security.
File Upload & Content Injection
Secure file handling, upload validations, and dynamic content areas vulnerable to manipulation.
API & Endpoint Testing
Evaluate REST APIs for token security, access control, rate limiting, and data leakage.
